A security threat has emerged targeting Snowflake database customers, attributed to a threat actor designated as UNC5537. Financial attackers target Snowflake users with stolen credentials. Learn how to protect your data with MFA and strong security practices.


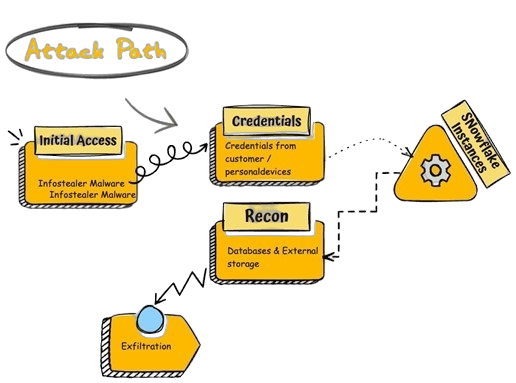
UNC5537 is characterized as a financially motivated threat actor primarily engaging in data theft and extortion activities. The group has been linked to the use of infostealer malware which facilitates the acquisition of user credentials from compromised systems.
These credentials are often sourced from historical breaches or malware infections dating back several years, demonstrating the long-term implications of credential exposure[1][5].
The threat actor operates under a veil of anonymity, utilizing commercial VPN services to mask their origins.
Reports indicate that UNC5537 has targeted hundreds of organizations globally, with operations traced back to mid-April 2024.
Their tactics include posting stolen data for sale on cybercriminal forums, thereby applying pressure on victims to comply with extortion demands[1][2][5].
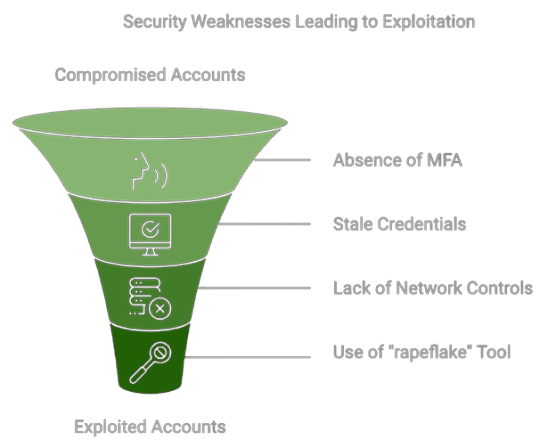
The attacks executed by UNC5537 have primarily exploited environments lacking multi-factor authentication (MFA). The following key factors have contributed to the success of their campaign:
The attackers employed a custom tool referred to as “rapeflake”, which facilitates reconnaissance within Snowflake environments by executing SQL queries to gather sensitive information about users and their roles[5].
The tactics used by UNC5537 can be mapped to several techniques within the MITRE ATT&CK framework:
These mappings illustrate how UNC5537 aligns with established attack patterns recognized in cybersecurity frameworks, underscoring the importance of robust security measures.
In response to this ongoing threat campaign, Snowflake has issued several recommendations aimed at bolstering customer security:

Snowflake has also provided indicators of compromise (IoCs) and investigative queries to assist customers in identifying potential threats[1][2][4].
TThe UNC5537 campaign against Snowflake database customers highlights the vulnerabilities inherent in cloud-based environments, particularly concerning credential management.
Organizations must prioritize implementing comprehensive security measures such as MFA, password lifecycle management and vigilant monitoring practices.
By adopting these strategies, businesses can better protect themselves against identity-based attacks and safeguard their sensitive data from malicious actors.
The evolving nature of cyber threats necessitates continuous vigilance and proactive measures in the face of emerging threats like UNC5537.
[1] https://www.threatkey.com/resource/unc5537-threat-actor-targeting-snowflake-databases-for-data-theft-and-extortion-indn
[2] https://thisweekhealth.com/news_story/unc5537-targets-snowflake-customer-instances-for-data-theft-and-extortion-google-cloud-blog/
[3] https://www.techtarget.com/searchsecurity/news/366587176/Threat-actor-targeting-Snowflake-database-customers
[4] https://www.dataprivacyandsecurityinsider.com/2024/06/update-on-snowflake-cyber-threat/
[5] https://thehackernews.com/2024/06/snowflake-breach-exposes-165-customers.html
[6] https://www.hunters.security/en/blog/detect-threats-in-snowflake-unc5537
[7] https://www.reddit.com/r/snowflake/comments/1fmu9e6/investigating_unc5537_snowflake_database_threat/
[8] https://cloud.google.com/blog/topics/threat-intelligence/unc5537-snowflake-data-theft-extortion
Post Tags :
Share :

Assess. Measure. Fortify.
Keep Your Assets Safe With Our
Cutting-Edge Cybersecurity Solutions.
Developed by HACKTRONIAN