Learn how SBOMs enhance software security by providing transparency into components, dependencies, and risks, helping prevent supply chain attacks.

Software supply chain attacks are a growing threat to software security and integrity. These attacks exploit vulnerabilities in development, delivery, or maintenance processes, allowing attackers to access sensitive data, compromise systems, or manipulate software functionality.
A major challenge in mitigating these attacks is the lack of visibility into software composition and origin. Software products often rely on multiple dependencies, including proprietary, open-source, and outsourced components. Without a clear understanding of these elements, assessing risks, verifying trustworthiness, and applying security measures becomes difficult.

This is where Software Bill of Materials (SBOMs) play a crucial role. An SBOM is a standardized document that details software components, dependencies, versions, origins, licenses, and vulnerabilities. By providing a complete inventory of the software supply chain, SBOMs help stakeholders identify, track, and mitigate risks.
This white paper explores how SBOMs help prevent software supply chain attacks by addressing the following questions:
| Benefits of SBOMs | Challenges of SBOMs |
| Improves visibility into software supply chains | Increases complexity in software development |
| Enhances security and compliance | Potential risk of information leakage |
| Facilitates collaboration among stakeholders | Requires coordination across multiple parties |
| Supports software innovation and evolution | Relies on the accuracy of component data |
| Framework/Mandate | Description |
| NTIA Software Transparency Initiative | A multi-stakeholder effort to establish best practices and minimum SBOM requirements. |
| ISO/IEC 27036-5 | Part of the ISO/IEC 27036 series, specifying SBOM requirements for software security. |
| SPDX | A Linux Foundation project providing a standard format for software component and license tracking. |
| CycloneDX | A lightweight SBOM specification tailored for application security and supply chain integrity. |
| Executive Order 14028 | A U.S. directive aimed at strengthening federal cybersecurity through SBOM adoption. |
SBOMs mitigate software supply chain risks by enabling:
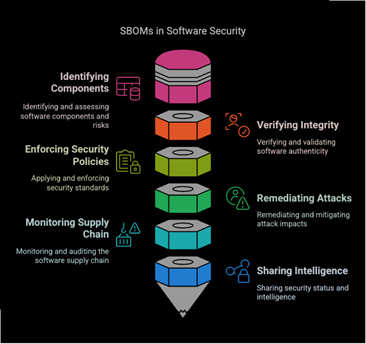
In 2017, a critical remote code execution vulnerability (CVE-2017-5638) in Apache Struts allowed attackers to exploit systems by sending malicious HTTP requests. The breach impacted Equifax, leading to the theft of millions of customers’ personal data.
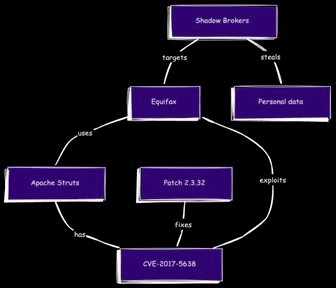
How SBOMs Could Have Prevented the Attack
Had Equifax maintained SBOMs, it could have:
By leveraging SBOMs, organizations can reduce their exposure to such attacks.
SBOMs enhance software security by providing transparency into software components, dependencies, and risks. While they introduce challenges such as complexity and data quality concerns, they remain a vital tool for mitigating software supply chain threats.
To maximize their effectiveness, SBOMs should be integrated with code analysis, testing, and monitoring processes. Their continuous evolution will further strengthen software resilience against supply chain attacks.
Adopting SBOMs is a crucial step toward fostering trust, compliance, and security in the modern software ecosystem.
Post Tags :
Share :

Assess. Measure. Fortify.
Keep Your Assets Safe With Our
Cutting-Edge Cybersecurity Solutions.
Developed by HACKTRONIAN