Discover why Software Bill of Materials (SBOMs) are now essential for large enterprises. Learn about supply chain risks, regulations (CRA, EO 14028), and how SBOMs enhance security and TPRM.

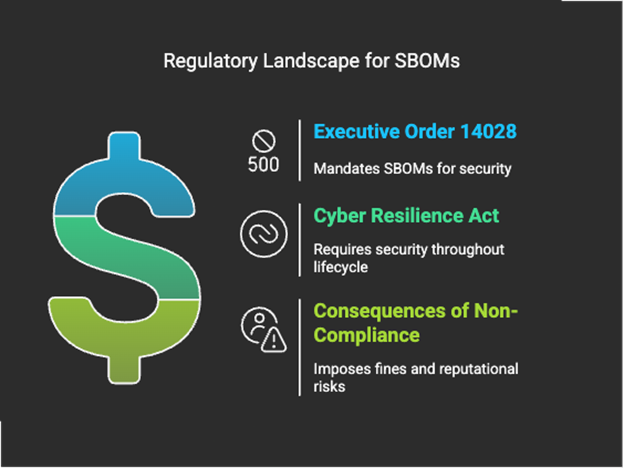
Software Bill of Materials (SBOM) has become a critical requirement for enterprise security. With increasing supply chain attacks, heightened regulatory pressures (e.g., CRA, EO 14028), and the need for stronger Third-Party Risk Management (TPRM), SBOMs are no longer a “nice-to-have” — they are essential for securing complex software ecosystems.
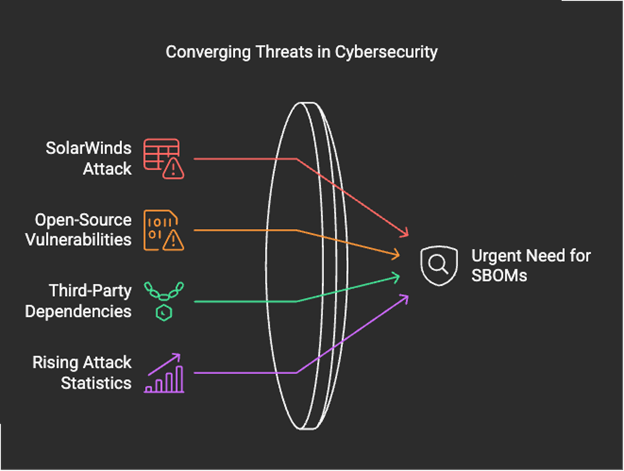
In recent years, supply chain attacks have emerged as one of the most significant threats to enterprise security. High-profile breaches like SolarWinds and Log4j have exposed the vulnerabilities within complex software ecosystems, pushing regulatory bodies and industry leaders to demand greater transparency and accountability.

For large enterprises, implementing SBOMs is no longer an option—it’s an operational and strategic necessity.
Future Outlook and Strategic Takeaways
Strategic Takeaways:

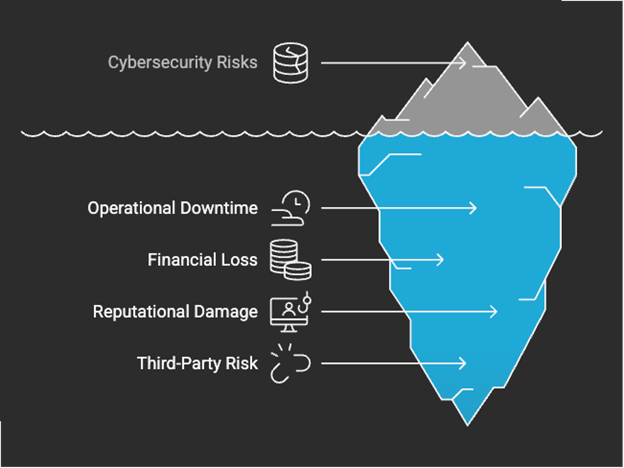
SBOMs have shifted from being a compliance checkbox to a strategic business necessity. For large enterprises, the path to secure software supply chains lies in adopting a structured and automated SBOM strategy.
Ready to strengthen your supply chain security? Contact our experts to learn how Deeproot Technologies can help you implement a robust SBOM framework.
Post Tags :
Share :

Assess. Measure. Fortify.
Keep Your Assets Safe With Our
Cutting-Edge Cybersecurity Solutions.
Developed by HACKTRONIAN